
Live cyber attack map FlowingData
A Fortinet Cyber Threat Assessment can help you better understand: Security Risk - which application vulnerabilities are being used to attack your network, which malware/botnets were detected, what phishing attacks are making it through your defenses and which devices are "at risk"— for security breach probability.
RealTime Cyber Attack Threat Map Cyber Security Memo
What is Lazarus RAT Attack? A new attack campaign led by the Lazarus threat actor group is seen employing new DLang-based Remote Access Trojan (RAT) malware. The attack attempts to exploit the Apache Log4j2 vulnerability (CVE-2021-44228) as initial access. Once compromised, it eventually creates a command and control (C2) channel. Read more

The Ultimate Guide to Cyber Threat Maps CISO Global (formerly Alpine
The Cybercrime Atlas initiative is about driving real impact and is a coordinated effort to create a chain of disruption in the world of cybercrime. We are excited to continue our work with private and public sector leaders to help make our digital world a safer place." News Summary

Top 15 Live Cyber Attack Maps for Visualizing Digital Threat Incidents
Threat Map is a feature of FortiADC that allows you to visualize the network attacks detected by FortiGuard Labs across the globe. You can filter the map by time range, attack type, severity, and source or destination country. Learn how to configure and use Threat Map to monitor and protect your network.
Real Time Cyber Threat Maps YouTube
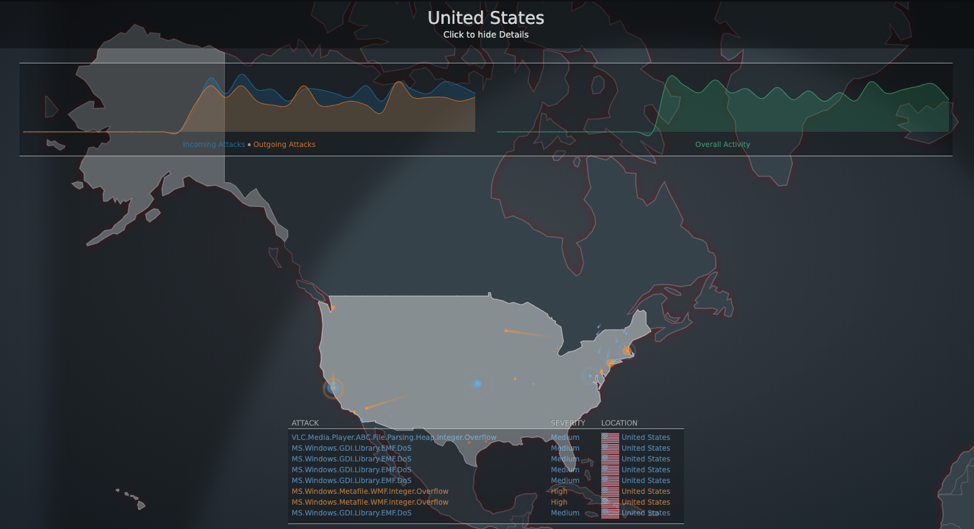
Is your network security keeping up with the latest threats? Request a free threat assessment today and find out about your vulnerabilities, user productivity, and network performance. ATTACK LOCATION SEVERITY Click for Details Incoming Attacks Outgoing Attacks Overall Activity Quick Links

RealTime Threat Maps ControlTrends
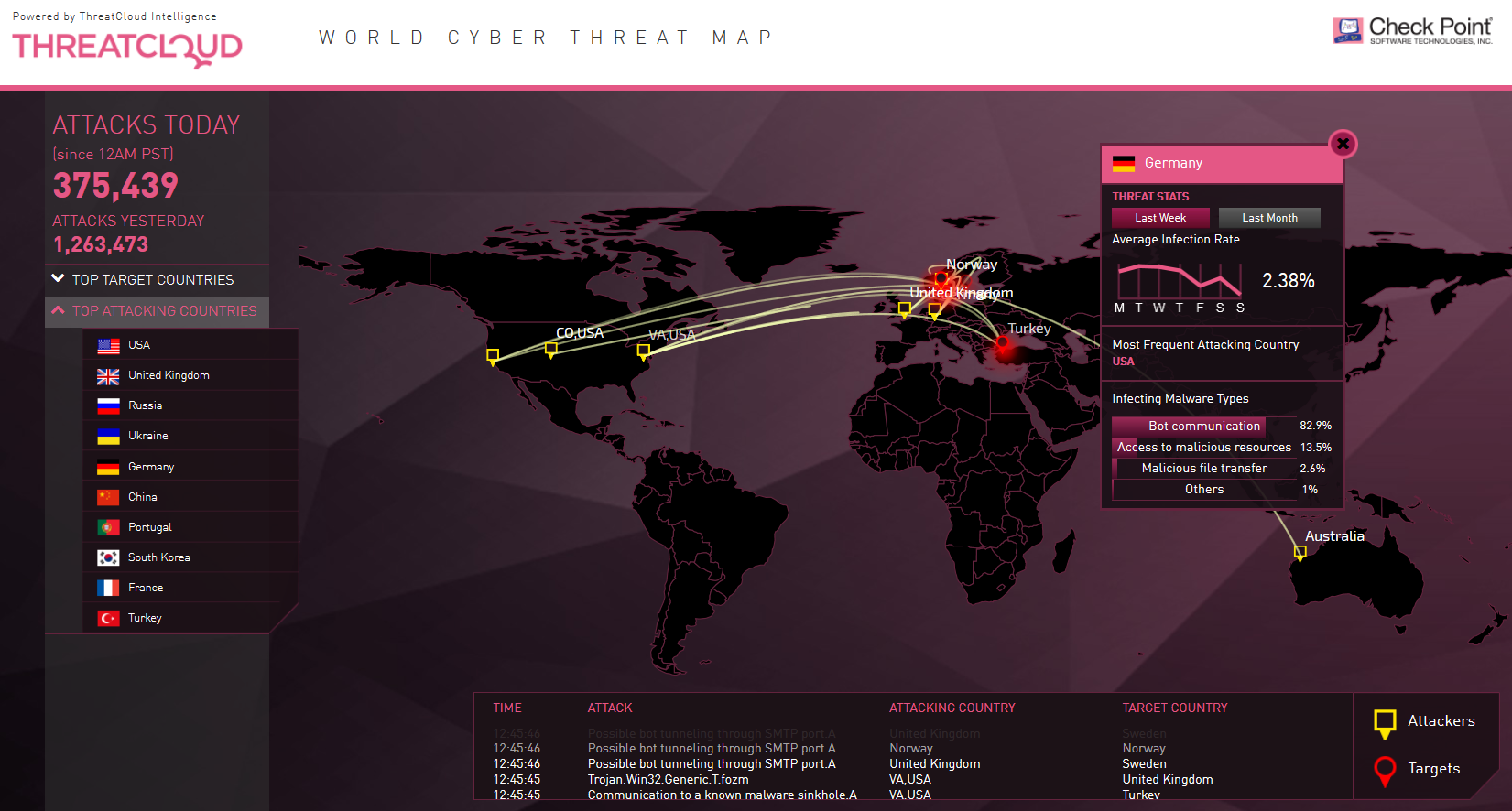
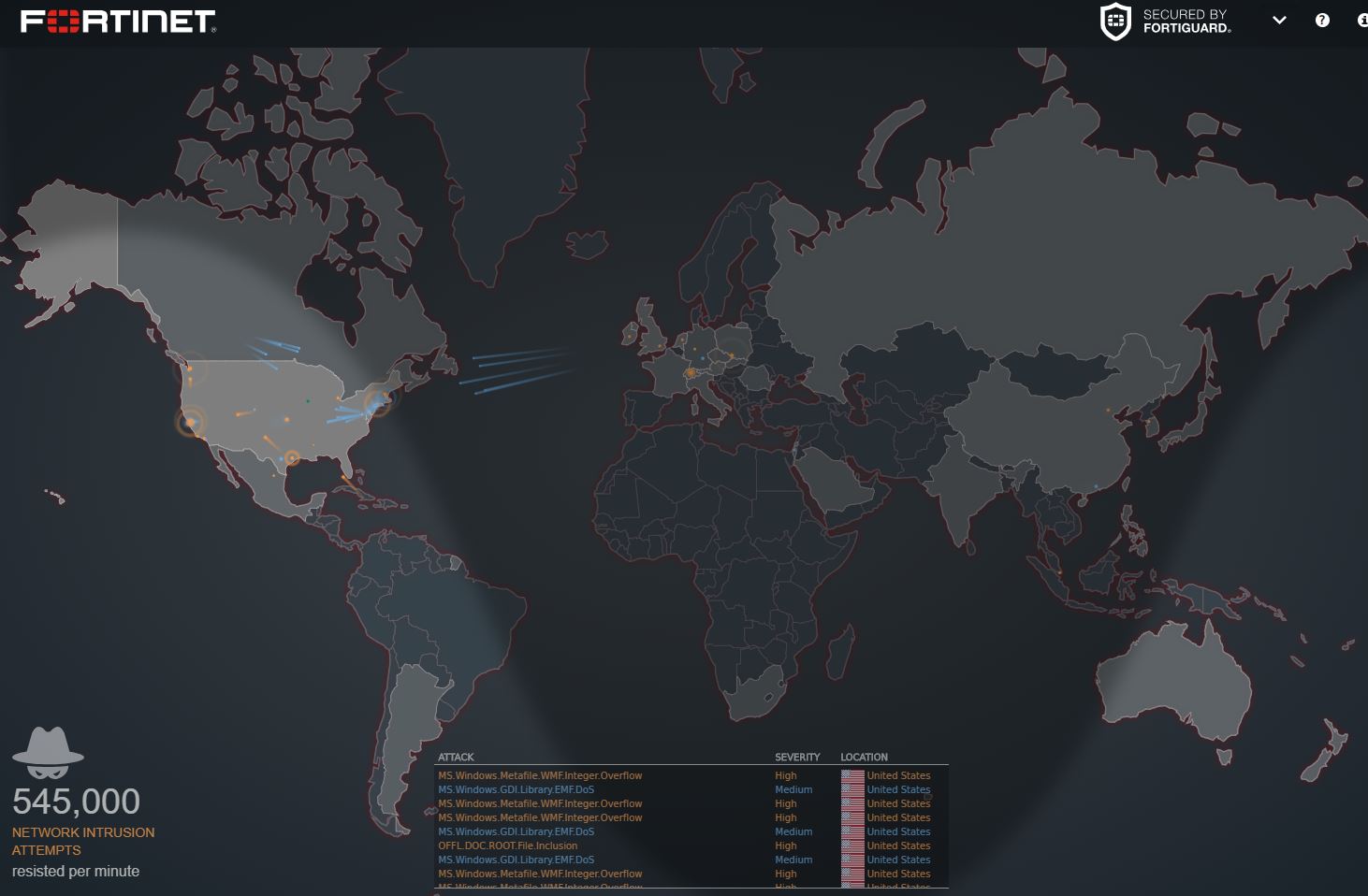
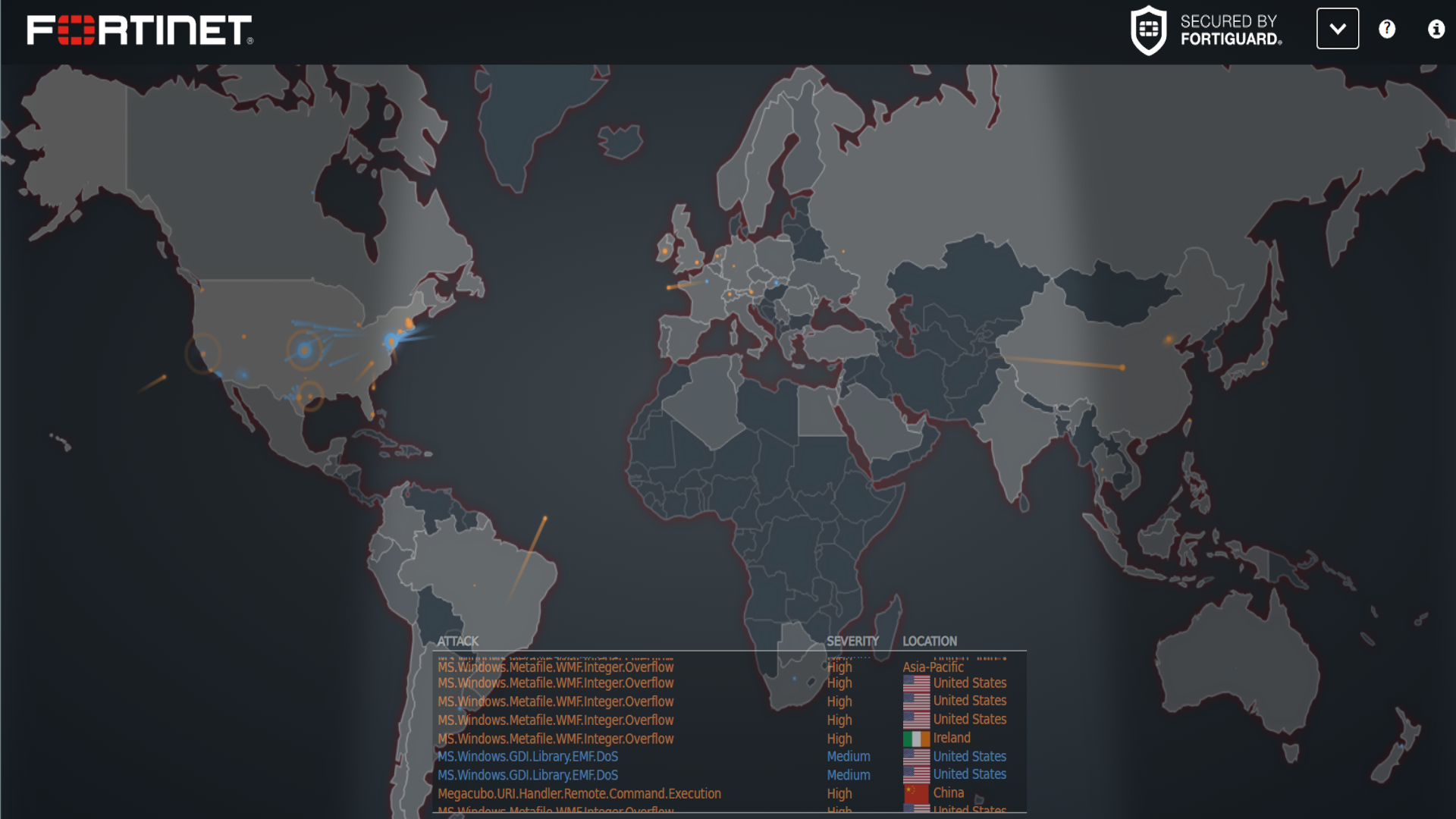
Fortinet Threat Map The Fortinet Threat Map provides live updates on threats such as malware, botnets, and DDoS attacks. Utilizing its extensive global threat intelligence network,.
globální podvod paprsek cyber threat map Usnadnit ret budoucnost
The Threat Map displays network activity by geographic region. From this window, you can see a global map that shows threats in real-time from specific countries: In the top-right corner of the window, you can select: now —View incoming threats in real-time. 1 hour —View a snapshot of incoming threats from the last hour. Previous Next
The Ultimate Guide to Cyber Threat Maps CISO Global (formerly Alpine
5.2.0. Attack Map. Attack Map is a visual representation of the entire network showing real endpoints, Decoy VMs, and ongoing attacks. The nodes on the map are color-coded by severity. , and Gateway. Click to view the attack history including AttackerStart TimeIncident ID.

Track Cyber Attacks Happening All Over The World Using These Maps
Is your network security keeping up with the latest threats? Request a free threat assessment today and find out about your vulnerabilities, user productivity, and network performance. ATTACK LOCATION SEVERITY Click for Details Incoming Attacks Outgoing Attacks Overall Activity Enlaces rápidos
Saturar prosperidad Inspector cyber attack map Paloma Un fiel
Fortinet's cyber attack map looks similar to the one from Norse and appears to show a playback of recorded events. As the attacks are displayed, a rotating breakdown of various stats.

Cyber Hitech Century
What are cyber attack threat maps? How do cyber Attacks work? 10 Cyber Attack Maps 1.Kaspersky Cyber Attack Map 2. Norse Attack Map 3. Arbor Networks 4. Digital Attack Map 5.Akamai

9 Interesting Ways to Watch Cyberattack in Realtime Worldwide
Fortinet Threat Map | Managed IT Professionals Check out the Fortinet Threat Map and watch real time cyberattacks taking place from around the globe. Check out the Fortinet Threat Map and watch real time cyberattacks taking place from around the globe. Try Risk-Free [email protected] 201-300-3825 Company Company Overview Our Approach

Security Fabric Solutions Exclusive Networks Austria
Cybersecurity Event/Threatgroup Trackers. The CyberWar Map and Other Cybersecurity Trackers. , Digital and Cyberspace Policy Program, Council on Foreign Relations. APT Groups and Operations spreadsheet. , Center for Strategic and International Studies (CSIS) Targeted Cyberattacks Logbook.
Top 8 Cyber Threat Maps To Track Cyber Attacks
To help you and your business feel confident in your ability to protect yourself against the threats that continue to come our way, this report looks back on the cyber threat landscape of the first half of 2022 using our global array of sensors monitored by FortiGuard Labs. Here's what we learned: Ransomware Roundup:

download geraseek
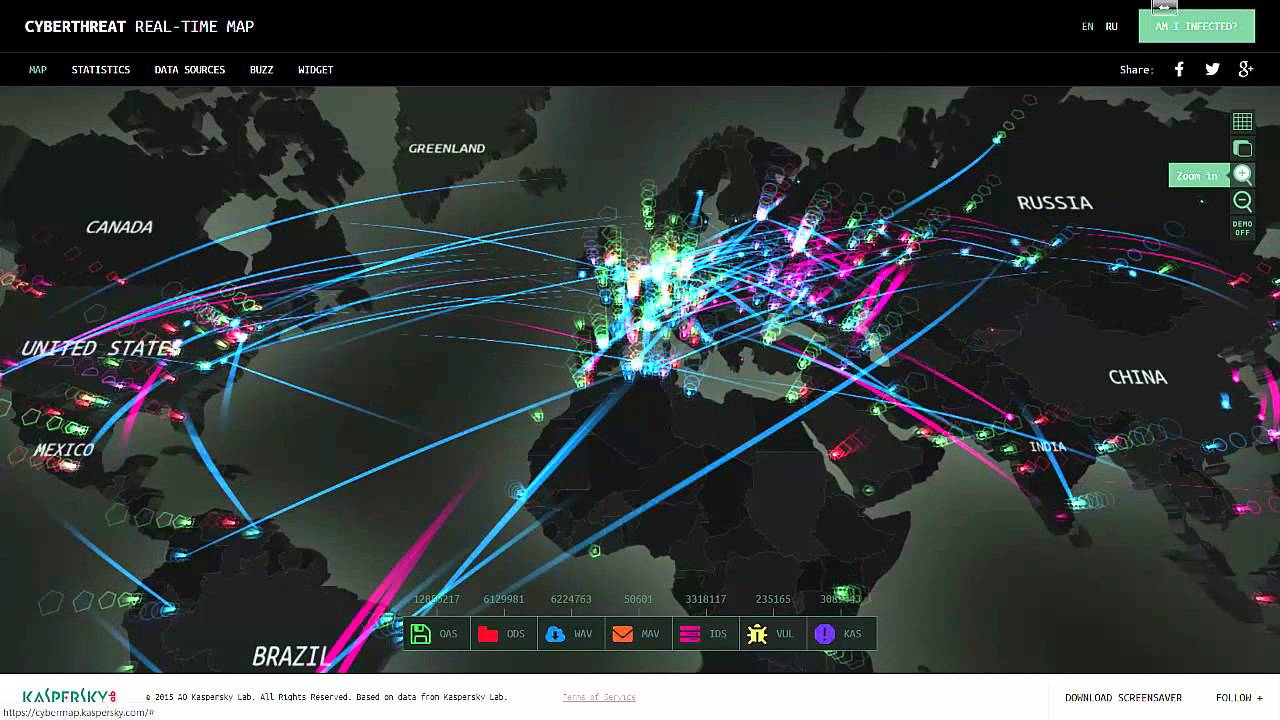
A cyber threat map, also known as a cyber attack map, is a real-time map of the computer security attacks that are going on at any given time. One of the most famous was released by the company Norse and went so viral, even among non-hackers, that it got its own story in Newsweek in 2015. The map itself looks like a global game of laser tag.

5 best malware tracker maps to see security attacks happen in realtime
FortiGuard Labs is Fortinet's in-house security research and response team, with over 10 years of proven threat prevention leadership, specializing in developing new adaptive defense tools to help protect against multi-vector zero day attacks. This global team oversees all of Fortinet's security services, delivering real-time, comprehensive.